- Online short course
Reconnaissance
In this course we look at the concept reconnaissance. We will cover the basic principles of reconnaissance, differences between passive and active reconnaissance, reconnaissance tools and the course ends with a quiz.
What is Reconnaissance?
Reconnaissance is a concept that is known for centuries, primarily for military strategical purpose.
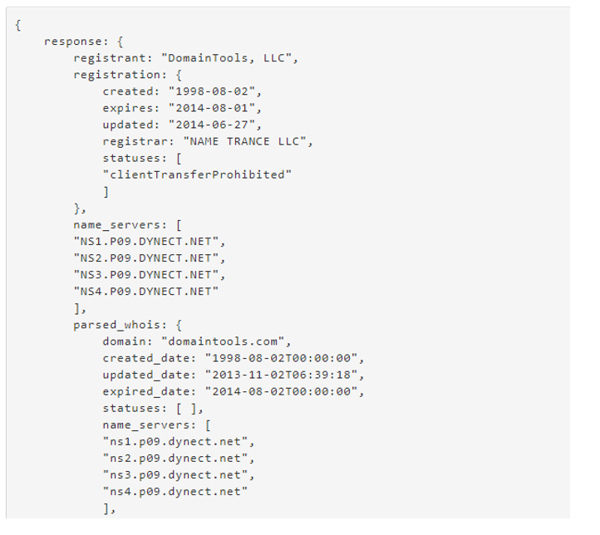
In IT security it is an important phase, in which an attacker uses for obtaining detailed information about their target. By using specific tools(which will be presented later in this course) for this phase of the attack, the attacker can interact with potential open ports, services running, etc on the targets network/systems or attempt to gain information without actively engaging with the network.

What is the kill chain?
Kill Chain is a structured model for attack purpose, originally used as a military concept related to the structure of an attack, consisting of the 7 phases.
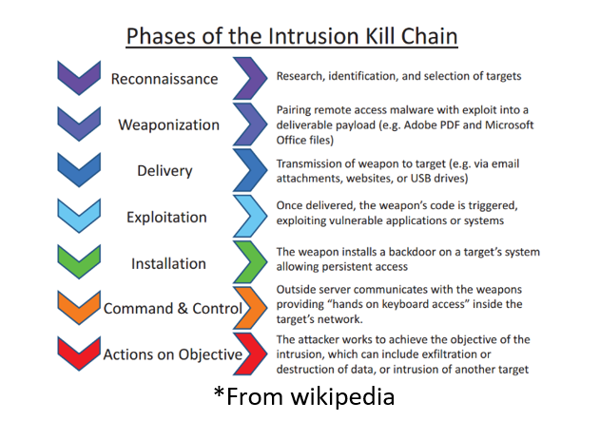
Each phase of this model has a purpose for the attacker’s final goals and for that there is many tools that an attacker can use for each phase. In this course will only focus on the reconnaissance phase and the tools for this phase.
Basic principles of Reconnaissance
Reconnaissance is the first step of the kill chain when doing a penetrations test or a malicious attack. This phase is done before the actual test or attack of the target network.

Differences between passive reconnaissance and active reconnaissance
An attacker will typically dedicate up to 75% of the overall work effort for a penetration test to the reconnaissance, as it is the phase that allows the target to be defined, mapped and explored for the vulnerabilities that may lead to exploitation.
There are two types of reconnaissance: passive reconnaissance and active reconnaissance.
Passive reconnaissance is when the attack recollects public information available on the internet, public database, social medias (Facebook, LinkedIn, X, Instagram,). Passive reconnaissance means that there is not a direct interaction between attacker and target.
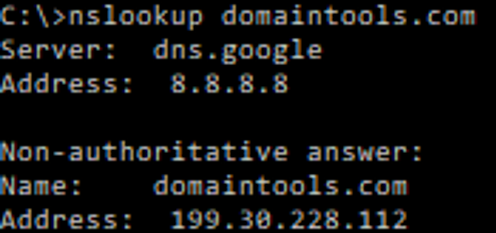
While active reconnaissance is when the attacker has a direct interaction with the targets network (port scan of the target network). The attacker can recollect more useful information about the network with active reconnaissance than with passive reconnaissance. The downside of actively interact with the target, is that the attacker has a higher risk of getting caught.
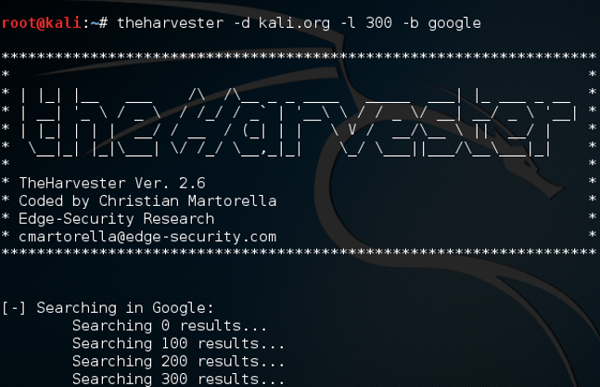
Tools that are used for Reconnaissance
Exercise
Now try these tools against a domain that you own/control.
Be cautious when doing active scan. Some Intrusion Detection Systems (IDS) might be triggered.